VMware Aria Cost powered by CloudHealth and Aria Automation for Secure Clouds
- Brock Peterson

- Mar 1, 2023
- 4 min read
Updated: Mar 7, 2024
In October 2018, VMware acquired CloudHealth, at that time, there were two products: CloudHealth and CloudHealth Secure State. Since then, CloudHealth has been rebranded as VMware Aria Cost powered by CloudHealth and CloudHealth Secure State is now Aria Automation for Secure Clouds.
CloudHealth was designed to provide Public Cloud costing details, while CloudHealth Secure State secures and ensures compliance for Public Cloud workloads. CloudHealth is Software as a Service (SaaS), running in AWS. CloudHealth Secure State is SaaS running in VMware Cloud, we'll explore them both in detail.
CloudHealth supports AWS, Microsoft Azure, Google Cloud Platform (GCP), Oracle Cloud Infrastructure (OCI), and Private Cloud (meaning on-prem vSphere), while VMware Cloud is in BETA. Once activated, you log into the portal and configure connections. For help setting up your data collections, check the User Guide here.
Once you're collecting data, you can use the dashboards to see your data, here we see our AWS Dashboard. To explore other available dashboards, click the AWS Dashboard dropdown.

We can see our cost history by service, with the ability to include/exclude services by selecting them. As you scroll down, you'll see additional details: EC2 usage, RDS usage, and S3 usage.
There are more Dashboards, Reports, and Assets in the left hand pane, but for me the most interesting feature is the Recommendations. Here you will find Savings Plans, Reservations, and Rightsizing details. Expanding EC2 Rightsizing will give you details on your AWS EC2 instances.

The Recommendation column makes recommendations based on usage. For example, CloudHealth is recommending that we terminate these EC2 instances because they aren't being used, see their CPU and Memory Scores.

The latest Rightsizing Recommendations can be found under Rightsizing (New).
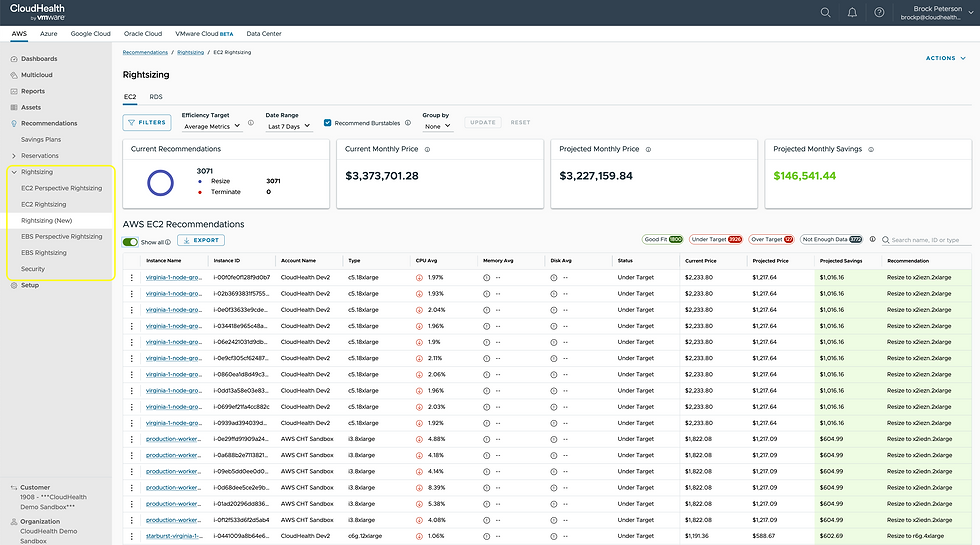
With a tab for both EC2 and RDS, you will see recommendations being made for each AWS Service, along with potential monthly savings if action is taken. Selecting an EC2 Instance will give you details around the recommendation, the available options, and relevant CPU, Memory, and Disk metrics.

Beyond Dashboards and Recommendations, there are dozens of reports available for each Public Cloud. Here you'll see all of the AWS Services we are consuming, along with several other available options.

To gain visibility into your other Public Clouds, configure their connections and explore their respective tabs at the top.
Let's now pivot to Aria Automation for Secure Clouds (formerly known as CloudHealth Secure State), SaaS designed to help manage risk in your Public Cloud environments. An architecture of Aria Automation for Secure Clouds can be found here.

There are several modules: Collection Module, Event Ingestion Module, Remediation Module, Alerts Module, Reports Module, and the Findings Module, which searches the Public Cloud data for findings by querying the databases and storing the results in AWS Elasticsearch. When findings are made, you can generate Alerts on them and make notifications via integrations with email, Slack, Splunk, and more.
As a VMware Cloud Service, once activated you will see it in your VMware Cloud Services Portal found at console.cloud.vmware.com.
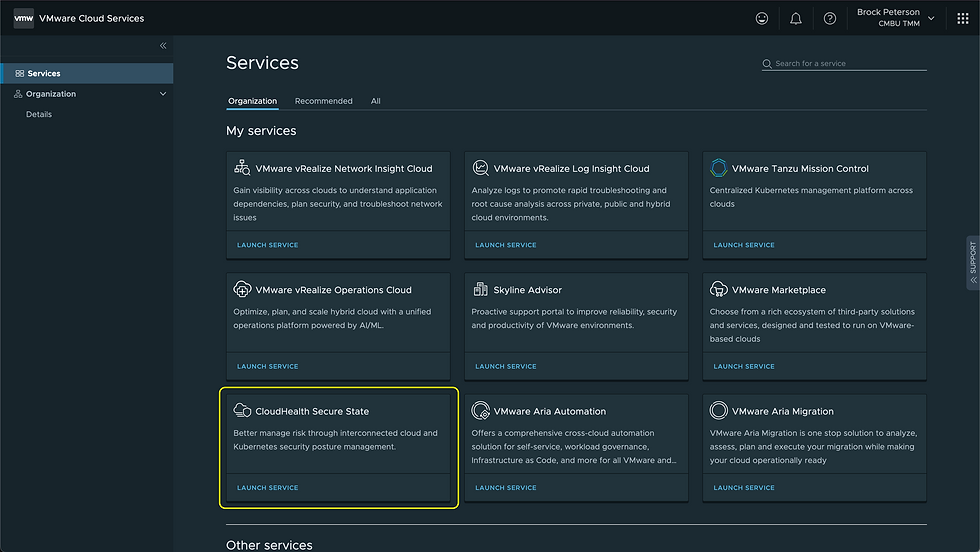
Click LAUNCH SERVICE to launch the service. CloudHealth Secure State supports AWS, Azure, and GCP Public Clouds.

Once your Cloud Accounts have been activated, it'll look something like this, with Findings, Top 10 Rules and Resources, and more. Every Finding corresponds to a monitored Public Cloud resource and is generated any time CloudHealth Secure State detects a configuration state on a Public Cloud resource in violation of an active security rule. There are two types of Findings:
Native findings: generated by CloudHealth Secure State and correspond to security rules created and maintained by the product development team.
Third-party findings: generated by external services such as Amazon GuardDuty or Microsoft Defender for Cloud, then ingested into CloudHealth Secure State through an inbound integration. See Third-party findings for more details.
Click on Findings at the top or within the Overview dashboard to get a list of your Findings.
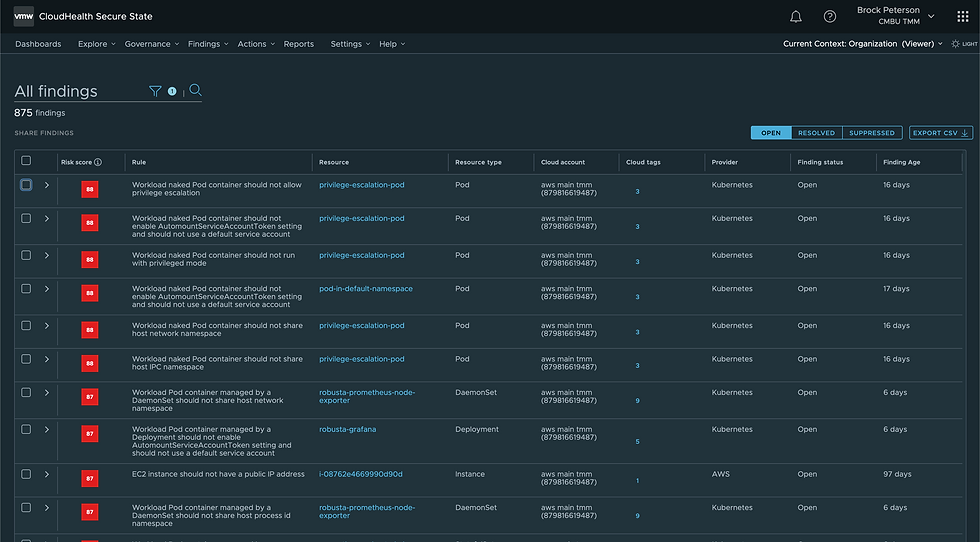
Select the Resource itself to explore the details.

Findings documentation can be found here. Findings are based on Rules contained in Frameworks, Frameworks being collections of Control Groups and Controls. The best explanation of Frameworks, Control Groups, Controls, and Rules can be found here and is re-stated below.

Framework is the top level compliance collection. The framework name will appear on the Compliance dashboard and findings pages, and in filters used throughout the product. Here's the HITRUST CSF Framework.
Control Group is a grouping of technical controls in a framework. This is intended for you to organize your controls into common themes. For example: mandatory and suggested controls or access and auditing controls. A framework requires a minimum of one control group. Major frameworks typically consist of multiple control groups.
Controls are the point requirements that must be adhered to. This is the technical control that CloudHealth Secure State can validate with rules. One or more controls may be assigned to a control group.
Rules are the policy checks that are running to validate and prove that you are adhering to a Control. A rule is not owned by the Framework as it can be associated to different controls in the organization
CloudHealth Secure State stays current with the latest compliance frameworks provided by AICPA, CCPA, CIS, CSA, EU, HITRUST, ISO, MITRE, NIST, PCI, and more. New versions of supported frameworks are added shortly after publication, while maintaining the two most recent versions.
Another important capability of CloudHealth Secure State is the ability to search and explore your entire environment, giving you the ability to find issues and establish violation blast radius in real time. The graph based output also allows you to view violations in context, with connected resources and services.
For more information on Aria Cost powered by CloudHealth and Aria Automation for Secure Clouds click the links in context, enjoy!













Comments